Understanding CORS: A Comprehensive Guide to Cross-Origin Resource Sharing
In today's interconnected web ecosystem, modern applications frequently need to communicate across different domains, making Cross-Origin Resource Sharing (CORS) a fundamental concept for web developers to master. As web applications grow more complex, integrating third-party APIs, fonts, or media, CORS ensures these interactions are secure and efficient. This guide explores CORS from its basic principles to practical implementation, helping developers enable secure cross-origin communications while maintaining robust security.
What is CORS?
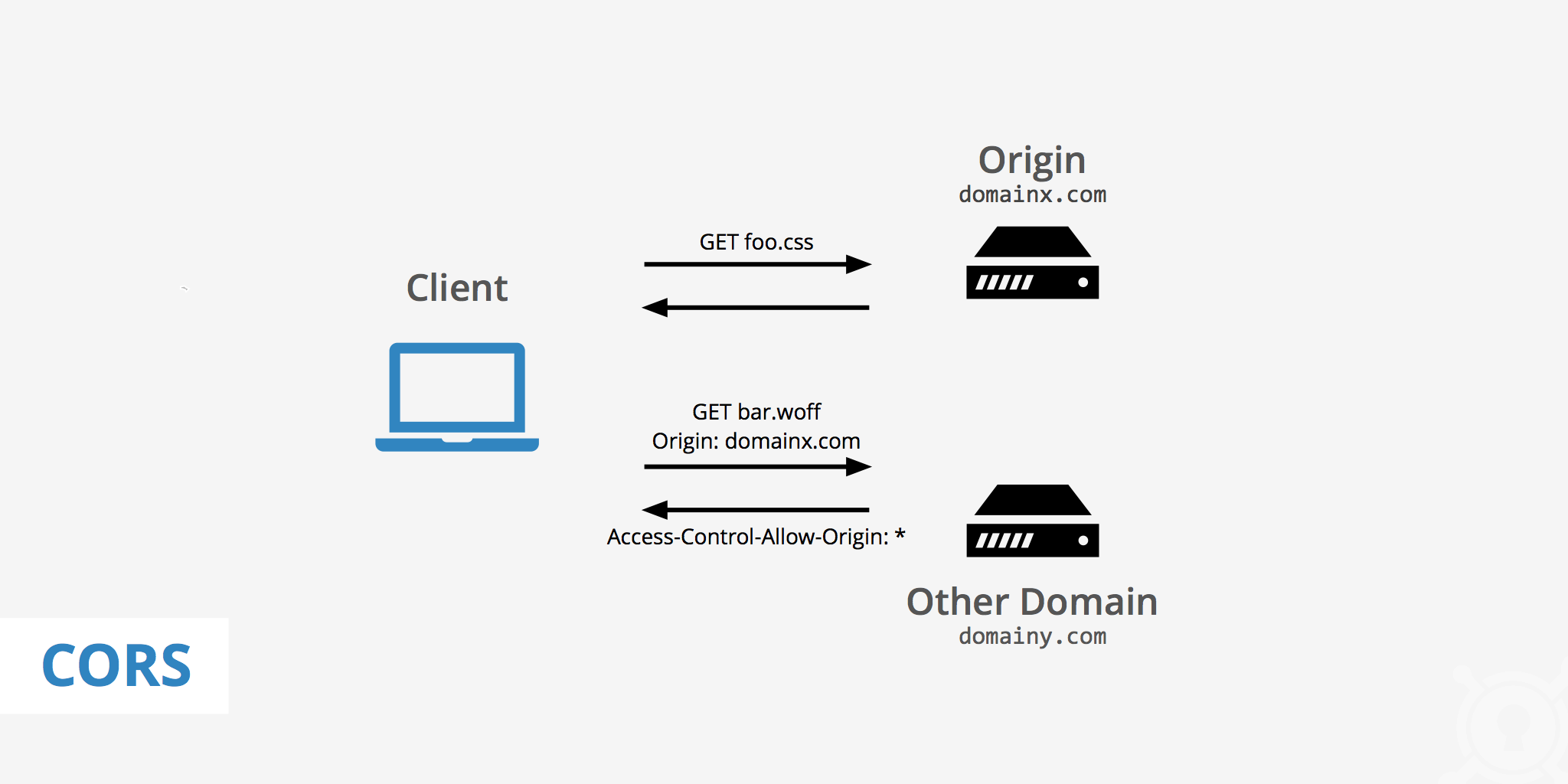
Cross-Origin Resource Sharing (CORS) is an HTTP-header-based mechanism that allows a server to indicate which origins (domain, scheme, or port) other than its own can access its resources. It enables web pages to make requests to a different domain than the one that served them, which is critical for modern web applications. For instance, a web application at https://myapp.com might need to fetch data from an API at https://api.example.com or load images from a content delivery network (CDN). Without CORS, browsers would block these requests due to the same-origin policy, a security measure designed to prevent malicious scripts from accessing sensitive data.
CORS is defined as part of the WHATWG's Fetch Living Standard and was formalized as a W3C Recommendation in January 2014 (W3C CORS Recommendation). It provides a standardized way to safely bypass the same-origin policy, balancing functionality with security.
The Same-Origin Policy
The same-origin policy is a browser security feature that restricts how a document or script loaded from one origin can interact with resources from another origin. An origin is defined by three components: the scheme (e.g., http or https), host (e.g., example.com), and port (e.g., 80 for HTTP, 443 for HTTPS). Two URLs are considered to have the same origin only if all three components match.
For example, consider a web page loaded from http://store.example.com/dir/page.html. The following URLs illustrate same-origin and cross-origin scenarios:
| URL | Same-Origin? | Reason |
|---|---|---|
http://store.example.com/dir2/new.html |
Yes | Only path differs |
https://store.example.com/page.html |
No | Different scheme (https) |
http://store.example.com:81/dir/page.html |
No | Different port (81 vs 80) |
http://news.example.com/dir/page.html |
No | Different host |
The same-origin policy prevents a web page from one domain from accessing data on another domain, protecting against attacks like cross-site request forgery (CSRF) and cross-site scripting (XSS). However, this restriction can limit legitimate cross-domain interactions, which is where CORS comes in.
How CORS Works
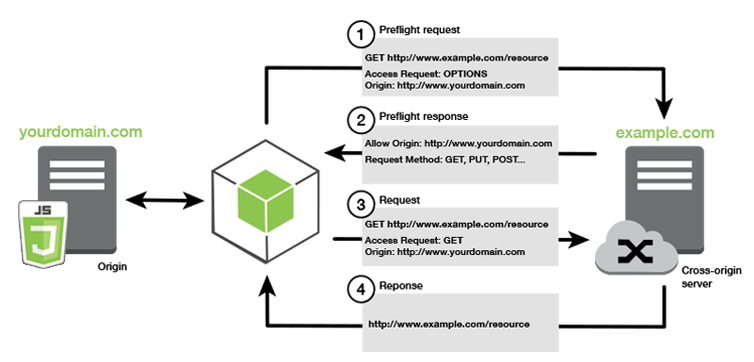
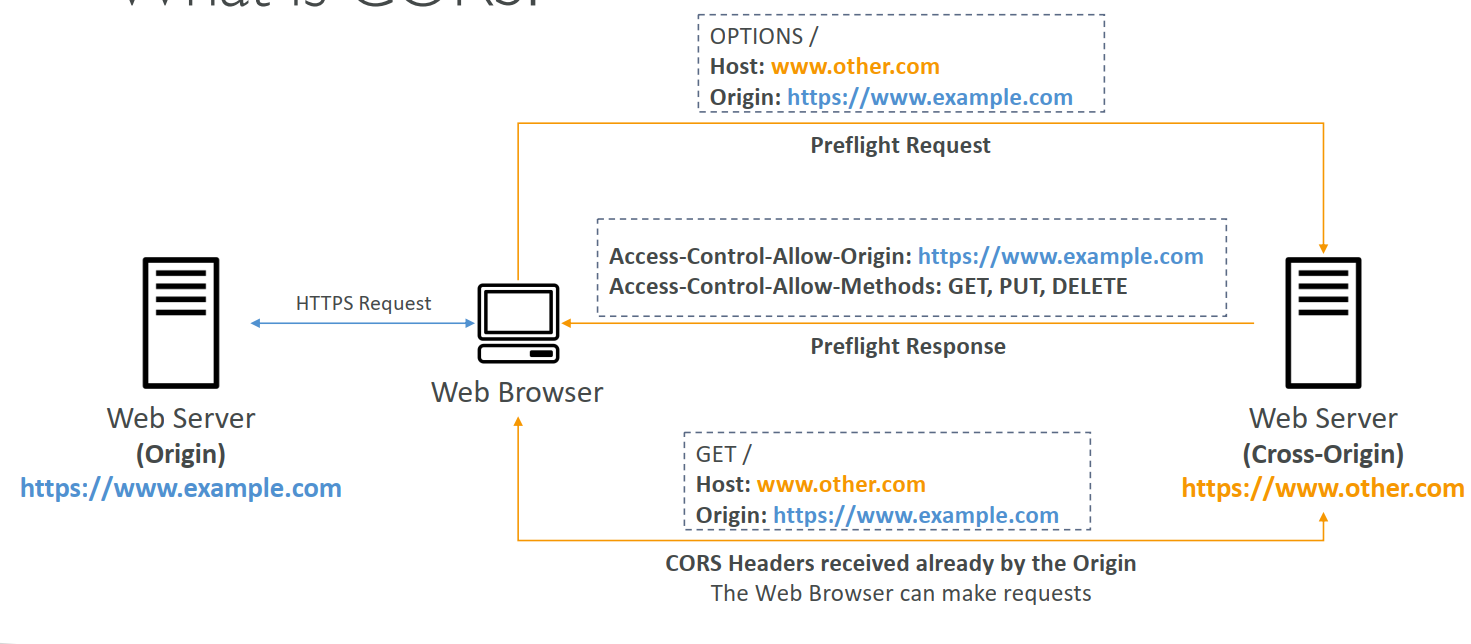
CORS operates by adding specific HTTP headers to requests and responses to negotiate access permissions between the browser and server. Here's a step-by-step overview of the process:
- Client Request: When a web page initiates a cross-origin request (e.g., using
fetch()orXMLHttpRequest), the browser includes anOriginheader indicating the requesting page's origin (e.g.,Origin: https://myapp.com). - Server Response: The server checks the
Originheader and responds with anAccess-Control-Allow-Originheader, specifying which origins are allowed to access the resource. For example,Access-Control-Allow-Origin: https://myapp.comallows requests from that specific origin, whileAccess-Control-Allow-Origin: *allows requests from any origin (less secure). - Browser Verification: The browser verifies the server's response. If the
Access-Control-Allow-Originheader includes the requesting origin or a wildcard, the browser processes the response. Otherwise, it blocks the response, and an error appears in the browser console.
Simple Requests
Some cross-origin requests, known as "simple requests," do not require a preflight check. These include requests using methods like GET, HEAD, or POST with specific content types (e.g., application/x-www-form-urlencoded, multipart/form-data, text/plain) and standard headers (e.g., Accept, Accept-Language, Content-Language). For example:
GET /data HTTP/1.1
Host: api.example.com
Origin: https://myapp.com
The server might respond with:
HTTP/1.1 200 OK
Access-Control-Allow-Origin: https://myapp.com
Content-Type: application/json
{"data": "example"}
Preflight Requests
For more complex requests—such as those using methods like PUT, DELETE, or custom headers (e.g., X-Custom-Header)—the browser sends a preflight request using the OPTIONS method to check if the server permits the actual request. The preflight request includes headers like:
Access-Control-Request-Method: The HTTP method of the actual request (e.g.,POST).Access-Control-Request-Headers: Any custom headers the actual request will use.
Example preflight request:
OPTIONS /data HTTP/1.1
Host: api.example.com
Origin: https://myapp.com
Access-Control-Request-Method: POST
Access-Control-Request-Headers: X-Custom-Header
The server responds with headers indicating allowed methods and headers:
HTTP/1.1 200 OK
Access-Control-Allow-Origin: https://myapp.com
Access-Control-Allow-Methods: POST, GET, OPTIONS
Access-Control-Allow-Headers: X-Custom-Header
Access-Control-Max-Age: 86400
The Access-Control-Max-Age header specifies how long (in seconds) the preflight response can be cached, reducing the need for repeated preflight requests.
Credentialed Requests
When a request includes credentials (e.g., cookies, HTTP authentication), the client must set credentials: "include" in fetch() or XMLHttpRequest.withCredentials = true. The server must respond with Access-Control-Allow-Credentials: true and specify an exact origin in Access-Control-Allow-Origin (not *). For example:
fetch('https://api.example.com/data', {
method: 'GET',
credentials: 'include'
})
Server response:
HTTP/1.1 200 OK
Access-Control-Allow-Origin: https://myapp.com
Access-Control-Allow-Credentials: true
Content-Type: application/json
{"data": "example"}
Note that credentialed requests are subject to browser policies on third-party cookies, which may impose additional restrictions.
CORS vs. JSONP
Before CORS, developers used JSONP (JSON with Padding) to bypass the same-origin policy. JSONP works by loading data via a <script> tag, but it has limitations:
- Limited to GET Requests: JSONP only supports
GETrequests, unlike CORS, which supports various HTTP methods. - Security Risks: JSONP can lead to XSS vulnerabilities if the external site is compromised, as it executes scripts directly.
- Error Handling: CORS provides better error handling through
XMLHttpRequestorfetch(), while JSONP relies on callbacks.
CORS is now the standard, supported by all modern browsers, while JSONP is largely deprecated except for legacy systems (CORS Browser Support).
Best Practices for CORS
Implementing CORS securely requires careful configuration. Here are key best practices:
- Specify Exact Origins: Avoid using
Access-Control-Allow-Origin: *for APIs handling sensitive data. Instead, list specific allowed origins (e.g.,https://myapp.com) to reduce the risk of unauthorized access. - Handle Preflight Requests: Ensure servers correctly respond to
OPTIONSrequests with appropriateAccess-Control-Allow-MethodsandAccess-Control-Allow-Headersheaders. - Set Appropriate Max-Age: Use
Access-Control-Max-Ageto cache preflight responses (e.g.,86400for 24 hours) to improve performance by reducing preflight requests. - Avoid Null Origins: Do not allow
nullinAccess-Control-Allow-Origin, as it can be exploited (e.g., viafile://requests orlocalhost). - Secure Credentialed Requests: For APIs requiring credentials, set
Access-Control-Allow-Credentials: trueand specify exact origins, avoiding wildcards. - Validate Headers: Only allow necessary headers in
Access-Control-Allow-Headersto minimize attack surfaces.
Example: Configuring CORS in a Node.js Server
Below is an example of enabling CORS in a Node.js server using the express framework:
const express = require('express');
const app = express();
// Enable CORS for specific origins
app.use((req, res, next) => {
const allowedOrigins = ['https://myapp.com', 'https://anotherapp.com'];
const origin = req.headers.origin;
if (allowedOrigins.includes(origin)) {
res.setHeader('Access-Control-Allow-Origin', origin);
}
res.setHeader('Access-Control-Allow-Methods', 'GET, POST, OPTIONS');
res.setHeader('Access-Control-Allow-Headers', 'X-Custom-Header');
res.setHeader('Access-Control-Max-Age', '86400');
if (req.method === 'OPTIONS') {
return res.status(200).end();
}
next();
});
app.get('/data', (req, res) => {
res.json({ data: 'Example response' });
});
app.listen(3000, () => console.log('Server running on port 3000'));
This code allows cross-origin requests from specified domains, handles preflight requests, and sets a 24-hour cache for preflight responses.
CORS in Cloud Services
Many cloud providers simplify CORS configuration:
- Amazon S3: Supports CORS configuration with up to 100 rules for allowed origins, methods, and operations (Amazon S3).
- Amazon API Gateway: Enables CORS for REST APIs with a single click in the console (Amazon API Gateway).
- Google Cloud Storage: Provides built-in CORS support for buckets, requiring no additional code for
XMLHttpRequest(Google Cloud Storage).
Historical Context
CORS was first proposed in 2004 by Tellme Networks for VoiceXML 2.1 to enable safe cross-origin data requests. It was formalized as a W3C Working Draft in 2006, renamed to "Cross-Origin Resource Sharing" in 2009, and became a W3C Recommendation in 2014. Its adoption has grown with the rise of modern web applications, replacing less secure methods like JSONP.
Conclusion
CORS is a cornerstone of modern web development, enabling secure and flexible cross-origin communication. By understanding its mechanics—HTTP headers, preflight requests, and credentialed requests—developers can build robust applications that integrate third-party resources while maintaining security. Following best practices, such as specifying exact origins and optimizing preflight caching, ensures both performance and safety. As web applications continue to evolve, mastering CORS remains essential for creating seamless, secure user experiences.